Embedded Security
Embedded security refers to the protection of embedded systems, their components, and the data they handle from unauthorized access, manipulation, or malicious attack. It involves the implementation of robust security measures to ensure the confidentiality, integrity, and availability of embedded systems and the sensitive data they handle.

Security challenges
Hitex develops customized security architectures that protect systems from unauthorized access, data breaches, and malicious attacks. Our security measures ensure the integrity, confidentiality and availability of sensitive data.
As an embedded software company, we are well aware of the critical role software plays in various industries, especially in sectors such as automotive, medical devices, industrial automation, and many others. With the increasing interconnectivity of devices and the rise of the Internet of Things (IoT), ensuring the security of embedded systems has become more crucial than ever.
The consequences of security breaches in embedded systems can be severe, ranging from compromising user privacy and data theft to disrupting critical infrastructure and even causing physical harm. As a result, governments, regulatory bodies, and industry standards organizations have established stringent security requirements and guidelines for embedded systems, such as EN TS 50701 for railway and ISO 21434 for automotive.
To meet these security challenges, the entire software development lifecycle must be addressed, from initial design and development to deployment, maintenance, and ongoing updates. And we can help you!
CIA Triade

One of the fundamental principles of embedded security is the concept of CIA, which describes the three essential requirements when we talk about the security of data and information:
- Confidentiality
- Integrity
- Availability
It is also crucial to integrate security considerations into the design phase of your embedded systems. Threat modeling and risk assessment techniques can help identify potential vulnerabilities and design flaws early on, allowing you to implement appropriate security controls from the outset.
Threat Analysis and Risk Assessment
The primary tool to define the approach of the development department is the Cyber Security Risk Analysis, in ISO 21434 it is called Threat Analysis and Risk Assessment (TARA). The goal of the TARA is to determine the high level cyber security requirements. The execution itself can be divided into a sequential process.
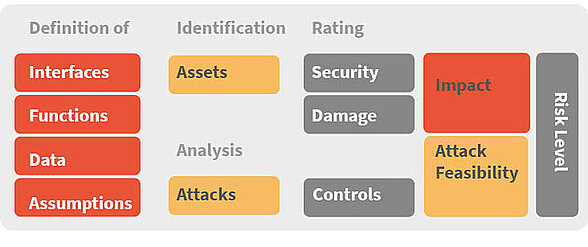
What Hitex can do for you
Staying informed about emerging security threats and vulnerabilities is essential. Regular security assessments, vulnerability scanning, and penetration testing can help identify weaknesses in your embedded systems and enable you to take proactive measures to mitigate them.
Hitex engineering services cover the entire embedded product development process. Benefit from our experience, whether you engage us for a sub-project or a complete project. Rely on a team of qualified developers for high quality development processes, also ISO 21434 compliant.
Embedded security is an ongoing effort that requires constant monitoring, updates and adaptation to the ever-changing threat landscape. With Hitex at your side in your embedded software development processes, you can build resilient systems that withstand attacks and contribute to a safer and more secure digital ecosystem.
Topics
Functional Safety
Hitex engineers have deep expertise in developing safety-critical software solutions that comply with safety standards like ISO 26262 and IEC 61508.

Embedded Security
Hitex develops security architectures that safeguard embedded systems from unauthorized access, data breaches, and malicious attacks.

Energy Efficiency
Our software engineers specialize in optimizing embedded systems for energy efficiency across various applications.

E-Mobility
Our software solutions enable enhanced performance, improve charging infrastructure, and intelligent energy management.

Standards
We help you to comply with safety standards such as ISO 26262 and safety requirements such as ISO 21434.
Microcontrollers
Everything at Hitex revolves around the microcontroller. Development, programming, software and safety & security.